ØxOPOSɆC Mɇɇtuᵽ [0x72] and [0x73] Challenges Write-up
“Based in Porto, the ØxOPOSɆC group was started by g33ks who are passionate about security. The meetup primary mission is to discuss and tackle upsurging security issues by leveraging the expertise and know-how of members of the group.” This is the write-up of the challenges of the 0x72 and 0x73 meetup editions, by @ArmySick and @Simps0n.
The meetup happens in a monthly-basis, feel free to join in.
[0x72] The loudest voice in the room is rarely the most right.
The loudest voice in the room is rarely the most right.
$ wget <ip_address>/omegalul.bmp
The resulting image was a modified version of the known XKCD sketch “Random Number”:

The modified imaged can be downloaded below:
How to solve it?
This seems like a steganography challenge. The first attempt was trying to run several steganography tools, including zsteg. However none of them worked throwing a variety of errors, but steghide threw a curious one:
steghide: the BMP file "omegalul.bmp" has a format that is not supported (biSize: 124).
After some searching found out this relevant StackOverflow Question:
biSize is the size of the BITMAPINFOHEADER only. It is 40 bytes.
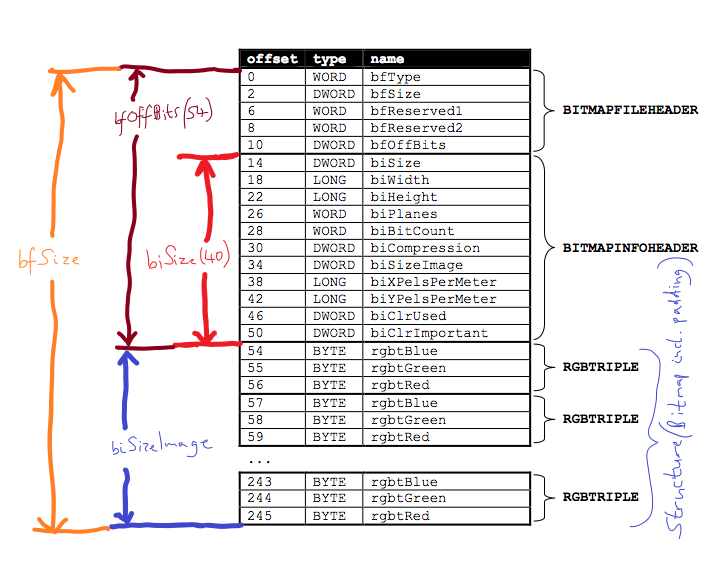
And, by just changing the value from 124 to 40 in the file header (OFFSET 14 / DWORD) with HxD Editor, we could run zsteg without any trouble:
b1,msb,bY .. text: "flag{Least_Significant_is_Most_Significant}\n"
flag{Least_Significant_is_Most_Significant}
[0x73] This is a military grade challenge!
Check the link <url> (+)

How to solve it?
Another steganography challenge. After a little manual analysis of the file using 010 editor, unknown padding at the end of the file appeared. Among the gibberish, an odd string appeared: dd02c7c2232759874e1c205587017bed.
After some searching and trial and error, it looked like an md5 hash of the string secret. But that was not a flag.
Moving on, a check for embedded files comes to mind. So, using $ binwalk -e challenge.jpg a ZIP file appeared: 46D41.zip with a file named dd02c7c2232759874e1c205587017bed inside.
For some reason fcrackzip did not properly worked on the zip (with both wordlist and brute-force).
Going traditional, I found several Python scripts on GitHub capable of brute-forcing ZIP password-protected files. Using military grade challenge as a hint, I guess it must be an “easy” password.
Using the following script, and the dictionary
SecLists/Passwords/Common-Credentials/best1050.txt.
The password was quickly found: admin123.
flag{ThisIsaOldTrickInTheBook}